Auth: OIDC
This feature is provided by the commercial plugin «Auth: OIDC», please purchase to useIntroduction
The Auth: OIDC plugin follows the OIDC (Open ConnectID) protocol standard, using the Authorization Code Flow, to allow users to sign in to NocoBase using accounts provided by third-party identity authentication service providers (IdP).
Activate Plugin
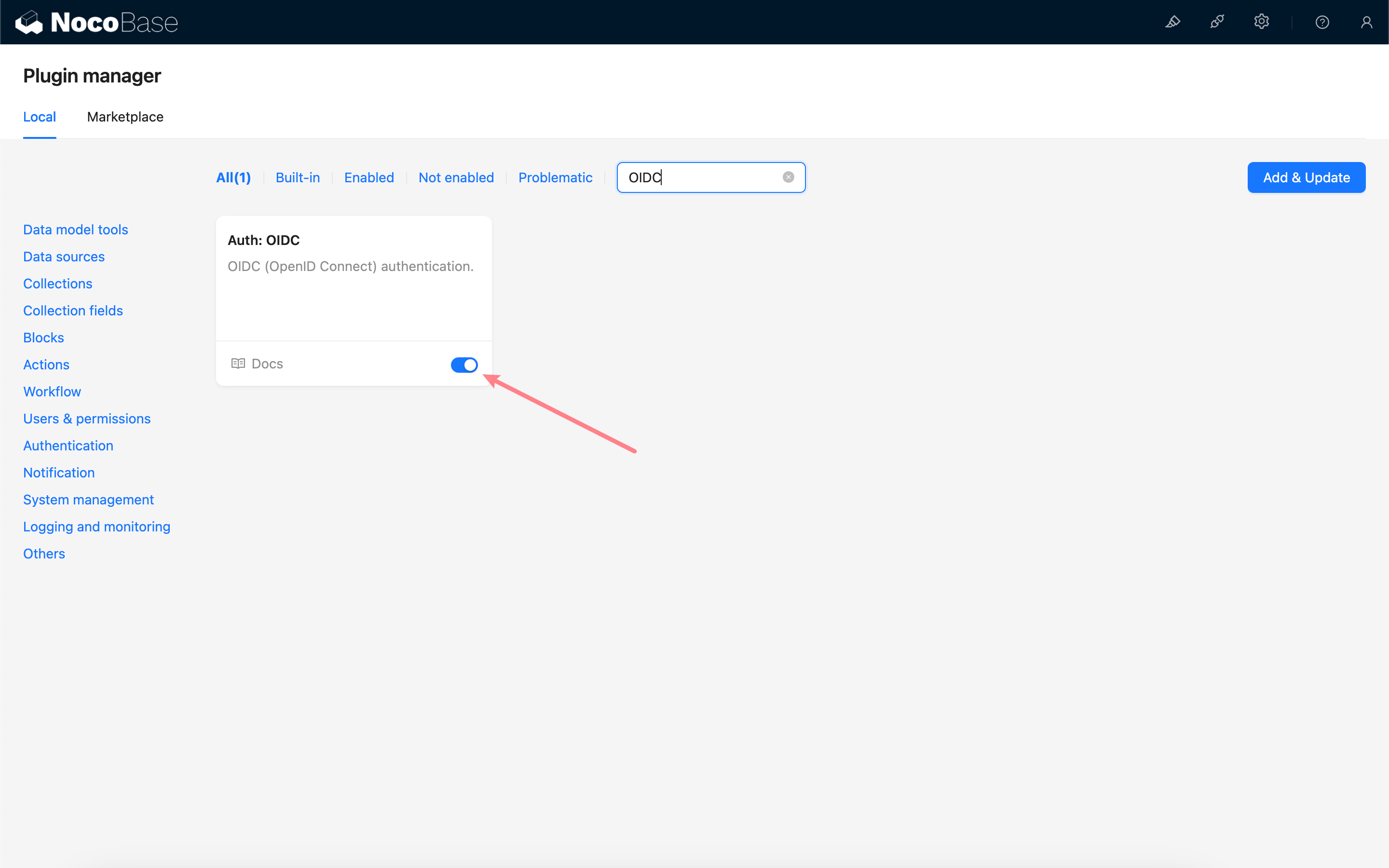
Add OIDC Authentication
Enter the user authentication plugin management page.
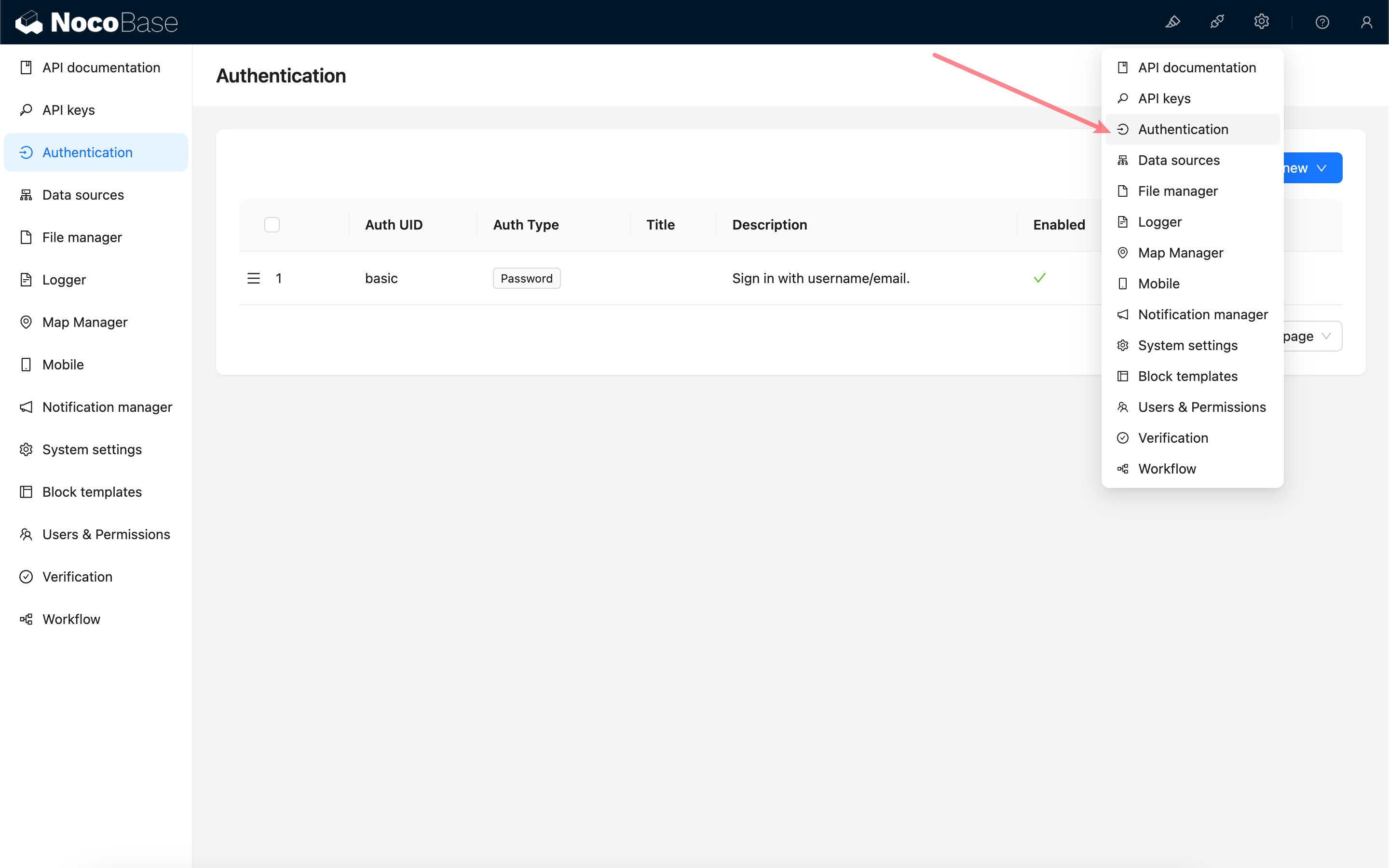
Add - OIDC
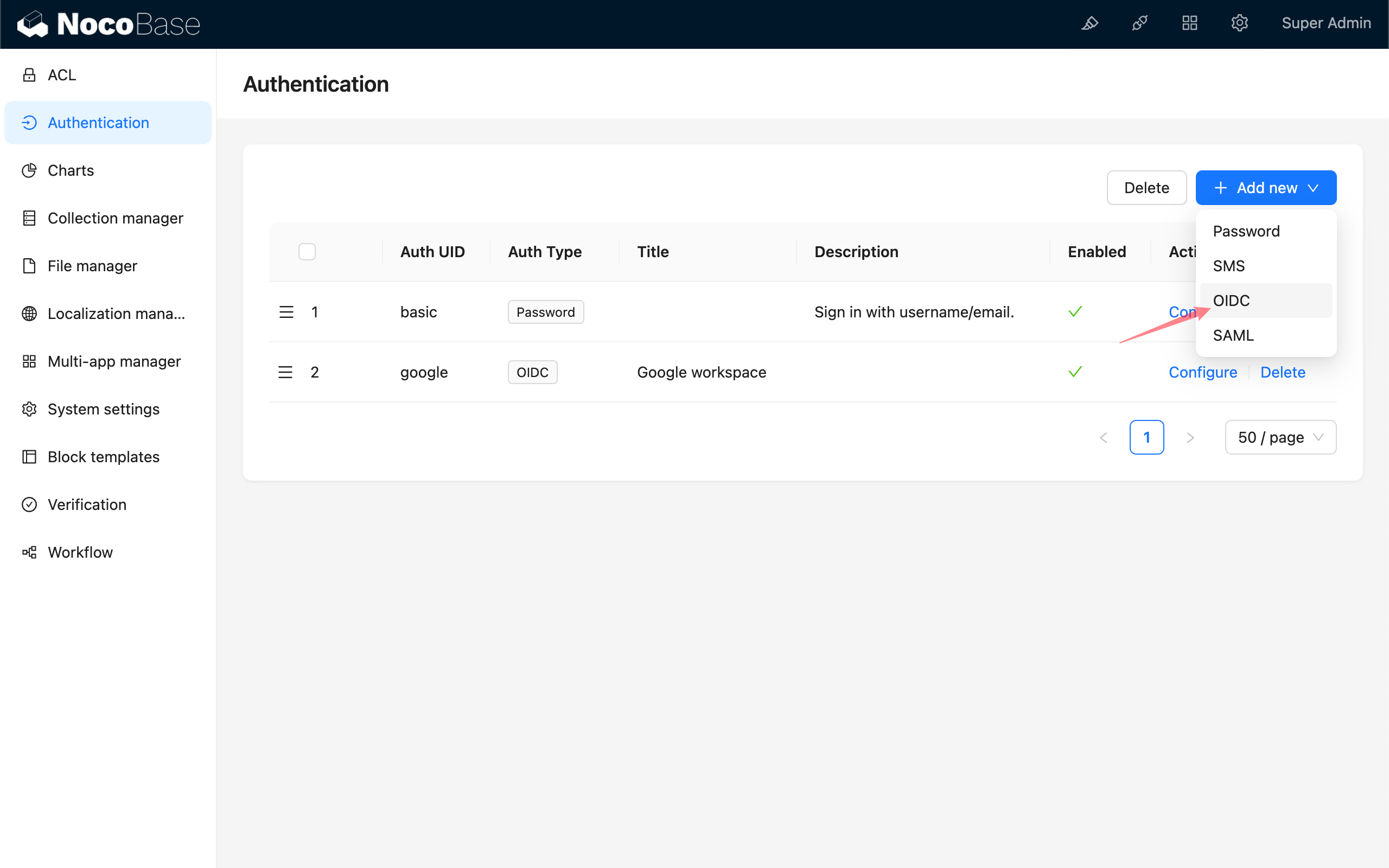
Configuration
Basic Configuration
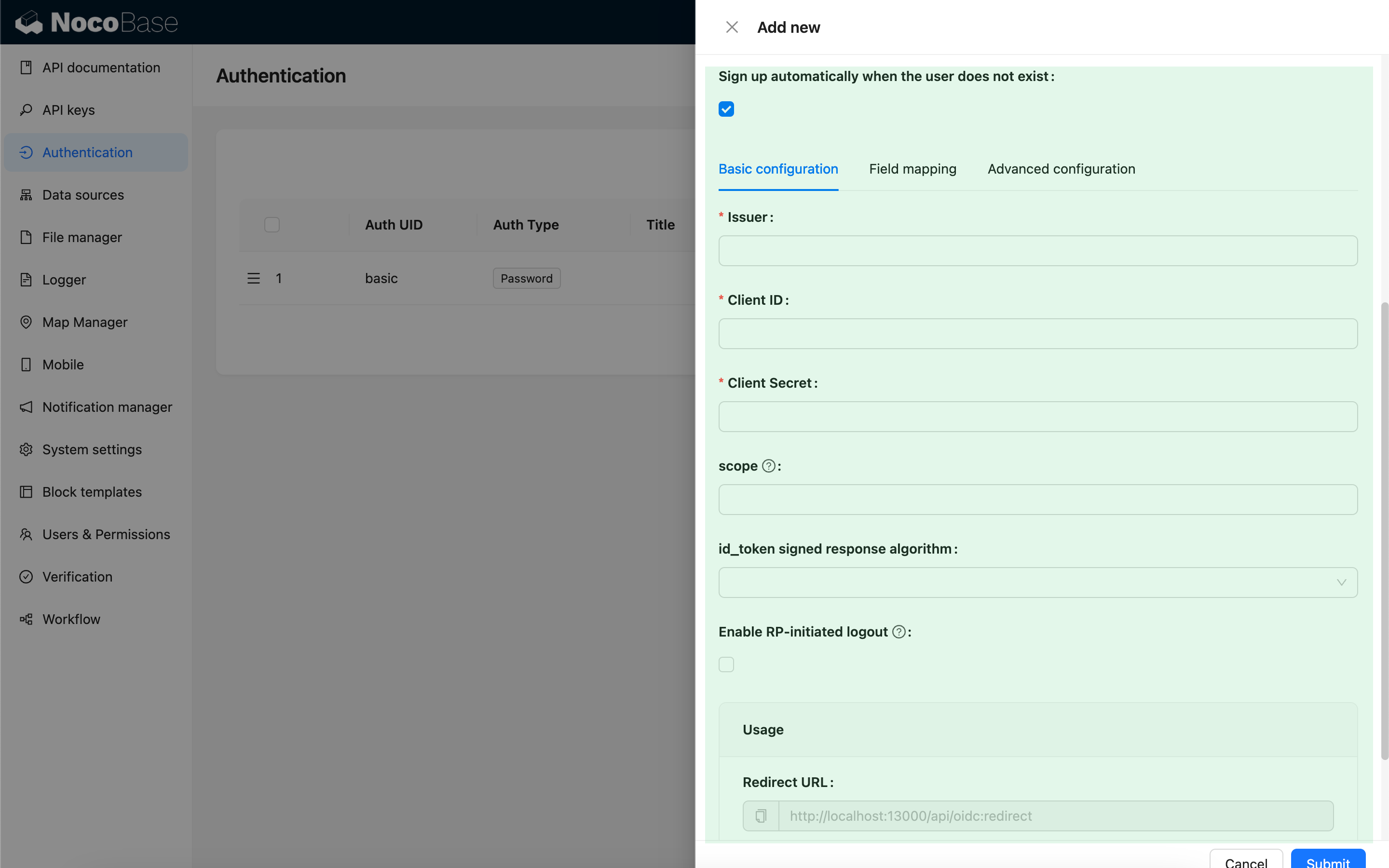
| Configuration | Description | Version |
|---|---|---|
| Sign up automatically when the user does not exist | Whether to automatically create a new user if no matching existing user is found. | - |
| Issuer | The issuer provided by the IdP, usually ending with /.well-known/openid-configuration. | - |
| Client ID | The Client ID | - |
| Client Secret | The Client Secret | - |
| scope | Optional, defaults to openid email profile. | - |
| id_token signed response algorithm | The signing algorithm for id_token, defaults to RS256. | - |
| Enable RP-initiated logout | Enables RP-initiated logout. Logs out the IdP session when the user logs out. The IdP logout callback should use the Post logout redirect URL provided in Usage. | v1.3.44-beta |
Field Mapping
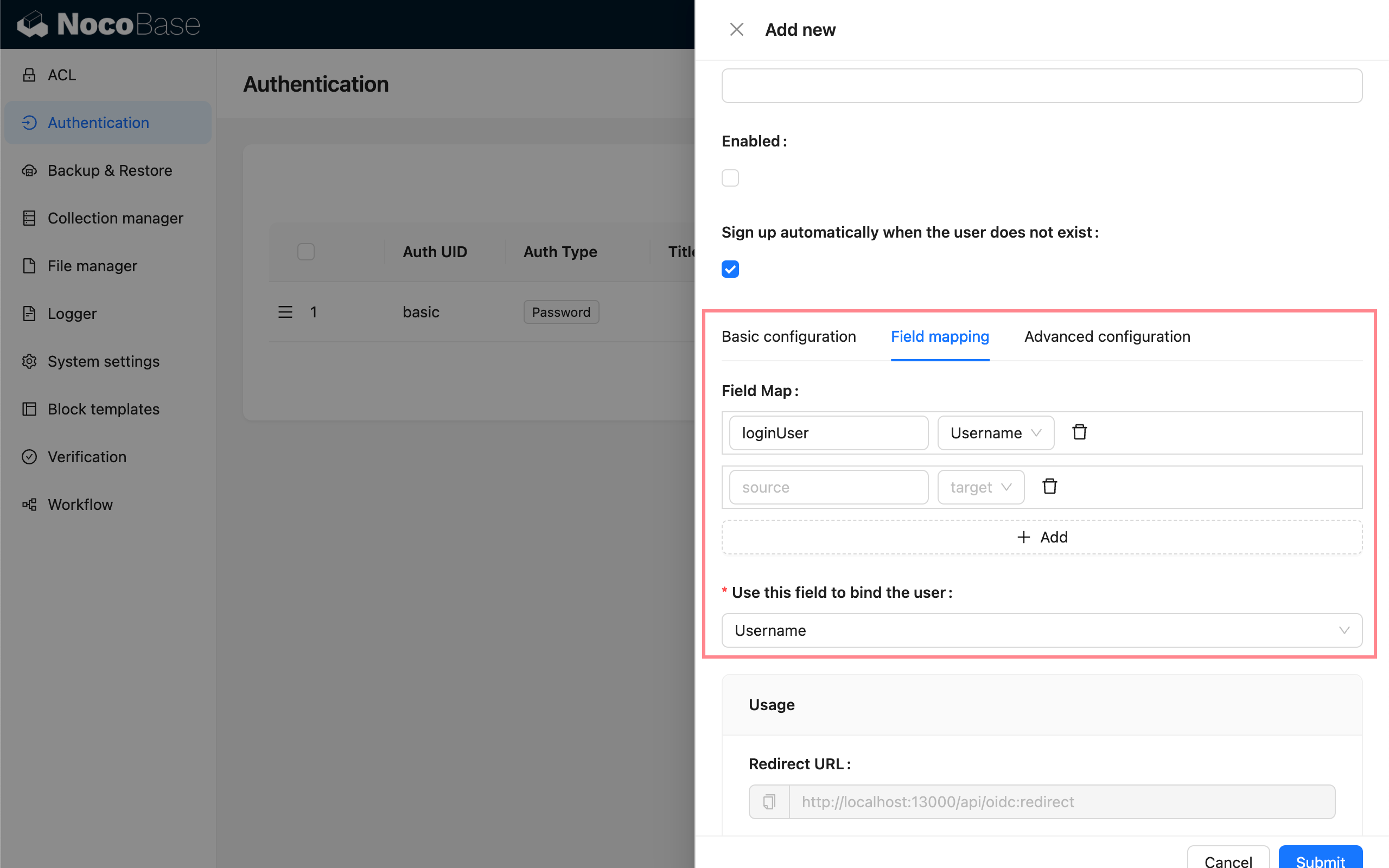
| Configuration | Description |
|---|---|
| Field Map | Field mapping. NocoBase supports mapping fields such as nickname, email, and phone number. The default nickname uses openid. |
| Use this field to bind the user | Used to match and bind with existing users. You can choose email or username, with email as the default. The IdP must provide email or username information. |
Advanced Configuration
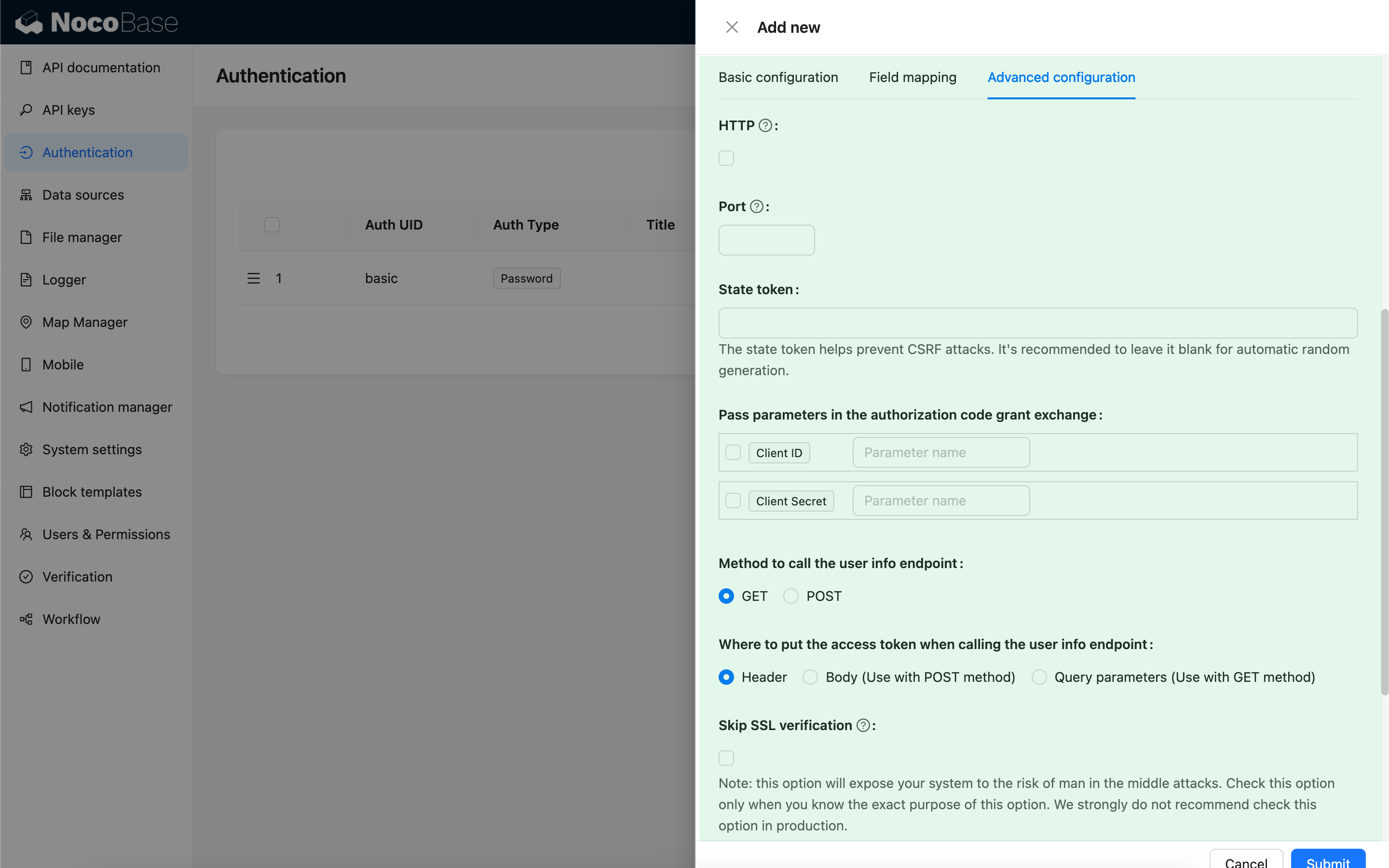
| Configuration | Description | Version |
|---|---|---|
| HTTP | Whether the NocoBase callback URL uses HTTP protocol, default is https. | - |
| Port | Port for the NocoBase callback URL, defaults to 443/80. | - |
| State token | Used to verify the request source and prevent CSRF attacks. You can provide a fixed value, but leaving it blank to generate random values by default is strongly recommended. If you use a fixed value, carefully evaluate your environment and security risks. | - |
| Pass parameters in the authorization code grant exchange | Some IdPs may require passing Client ID or Client Secret as parameters when exchanging a code for a token. You can select this option and specify the corresponding parameter names. | - |
| Method to call the user info endpoint | The HTTP method used when requesting the user info API. | - |
| Where to put the access token when calling the user info endpoint | How the access token is passed when calling the user info API: - Header - In the request header (default). - Body - In the request body, used with POST method.- Query parameters - As query parameters, used with GET method. | - |
| Skip SSL verification | Skip SSL verification when requesting the IdP API. This option exposes your system to risks of man-in-the-middle attacks. Only enable this option if you understand its purpose and implications. It is strongly discouraged in production environments. | v1.3.40-beta |
Usage
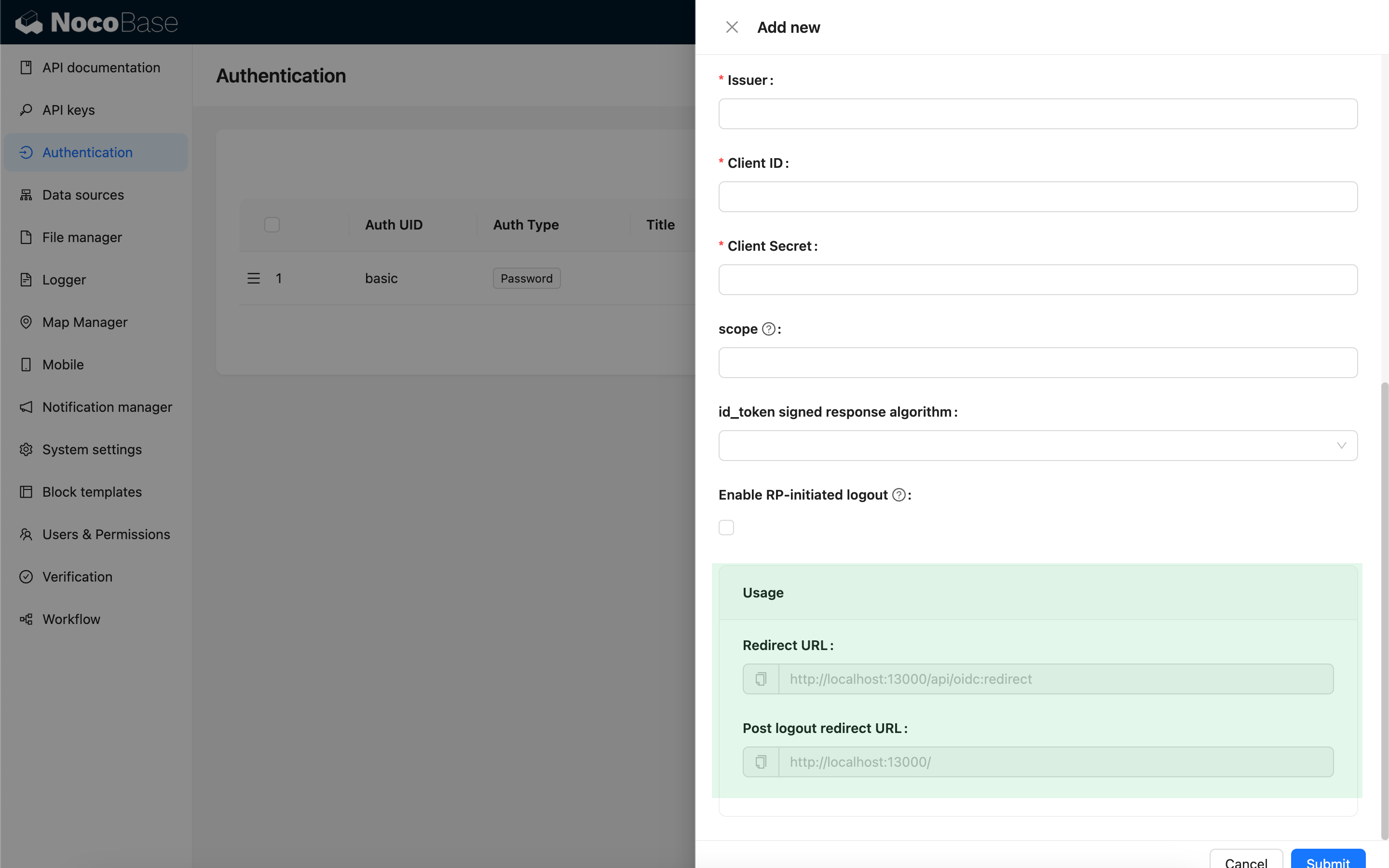
| Configuration | Description |
|---|---|
| Redirect URL | Used to configure the callback URL in the IdP. |
| Post logout redirect URL | Used to configure the Post logout redirect URL in the IdP when RP-initiated logout is enabled. |
When testing locally, use 127.0.0.1 instead of localhost for the URL, as OIDC login requires writing state to the client cookie for security validation. If you see a flash of the login window but fail to log in successfully, check the server logs for state mismatch issues and ensure the state parameter is included in the request cookie. This issue often occurs when the state in the client cookie does not match the state in the request.
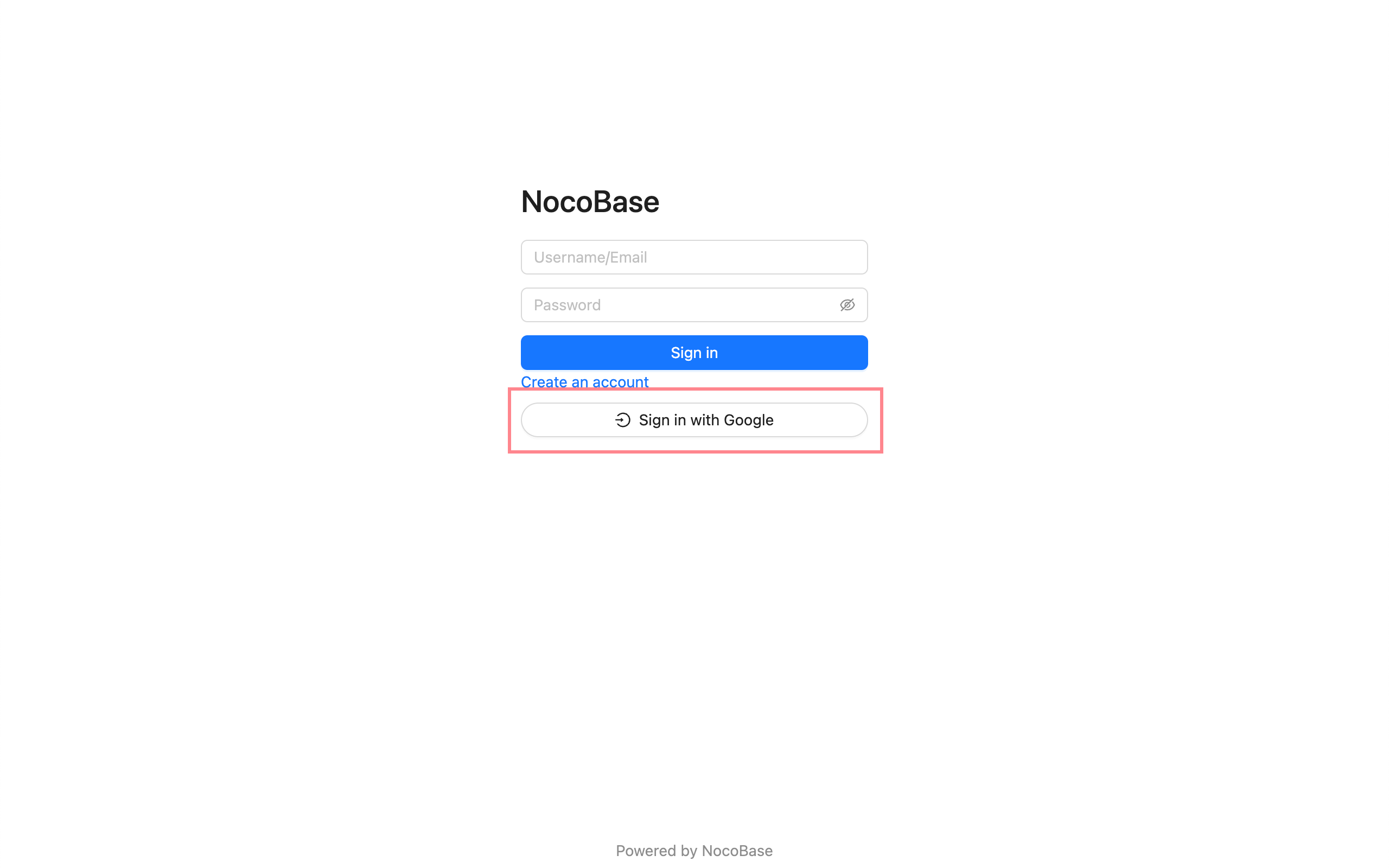
Login
Visit the login page and click the button below the login form to initiate third-party login.